Cybersecurity in the Age of IoT: Threats and Opportunities
IoT Cybersecurity: Understanding the Risks of Connected Devices
IoT cybersecurity is one of the most pressing concerns for modern businesses. The Internet of Things (IoT) has transformed industries, homes, and cities by connecting devices, appliances, sensors, and machines to the internet. While these devices offer unparalleled convenience and efficiency, they also create new security vulnerabilities that can be exploited by hackers.
IoT devices, such as smart thermostats, industrial sensors, wearable health monitors, and connected cameras, often lack robust security protocols. Many come with default passwords, outdated firmware, or limited encryption, making them easy targets for cyberattacks. Businesses need to understand that each connected device represents a potential entry point for cybercriminals.
Regulatory Compliance and Standards for IoT Security
As IoT devices proliferate across homes, businesses, and critical infrastructure, regulatory compliance has become a key concern. Governments and industry bodies are implementing standards to ensure device security, data privacy, and proper risk management. For instance, regulations like GDPR in Europe and the IoT Cybersecurity Improvement Act in the U.S. require organizations to maintain strict safeguards for connected devices. Businesses that adopt these standards not only protect themselves from cyber threats but also build customer trust and demonstrate responsible data management. Staying up-to-date with evolving compliance requirements is crucial for organizations leveraging IoT technology.
The Role of Artificial Intelligence in Securing IoT Networks
Artificial intelligence and machine learning are increasingly being used to secure IoT ecosystems. AI-powered security solutions can analyze massive amounts of device-generated data in real time, detect anomalies, and identify potential threats before they escalate. For example, AI can detect unusual traffic patterns in a network of smart cameras or industrial sensors, alerting security teams to possible breaches. By combining IoT devices with AI-driven monitoring, businesses can proactively mitigate risks, reduce downtime, and maintain operational continuity even as the number of connected devices continues to grow exponentially.
Common Threats in IoT Cybersecurity
Businesses face a variety of risks when adopting IoT technologies:
- Data Breaches: Sensitive information collected by IoT devices, including personal data, health records, and financial information, can be intercepted if security measures are weak.
- Botnets: Compromised IoT devices can be used to launch large-scale distributed denial-of-service (DDoS) attacks, disrupting services and networks.
- Device Hijacking: Hackers can gain control of smart devices, altering their functions or using them for malicious purposes.
- Privacy Violations: Inadequate IoT security can expose user behavior, location data, and private communications to unauthorized parties.
- Supply Chain Vulnerabilities: IoT devices often rely on third-party software or hardware, introducing risks if suppliers have weak security practices.
Opportunities in IoT Cybersecurity
Despite these risks, IoT cybersecurity also presents significant opportunities. By implementing proactive security measures, businesses can not only protect themselves but also build trust with customers and partners. Some key benefits include:
- Improved Threat Detection: AI-powered IoT security tools can detect unusual patterns, preventing attacks before they cause damage.
- Enhanced Operational Efficiency: Secured IoT networks allow businesses to leverage automation, real-time analytics, and predictive maintenance without compromising safety.
- Regulatory Compliance: Strong IoT cybersecurity practices help organizations comply with data protection regulations, avoiding fines and legal issues.
- Competitive Advantage: Businesses that prioritize IoT security can differentiate themselves as trustworthy and reliable in the digital marketplace.
How Businesses Can Protect Themselves
To strengthen IoT cybersecurity, organizations should adopt a multi-layered security strategy:
- Device Authentication: Ensure that every IoT device is authenticated before it joins the network. Use strong passwords and unique identifiers.
- Regular Firmware Updates: Keep devices updated to patch vulnerabilities and prevent exploits.
- Network Segmentation: Separate IoT devices from critical business systems to contain potential breaches.
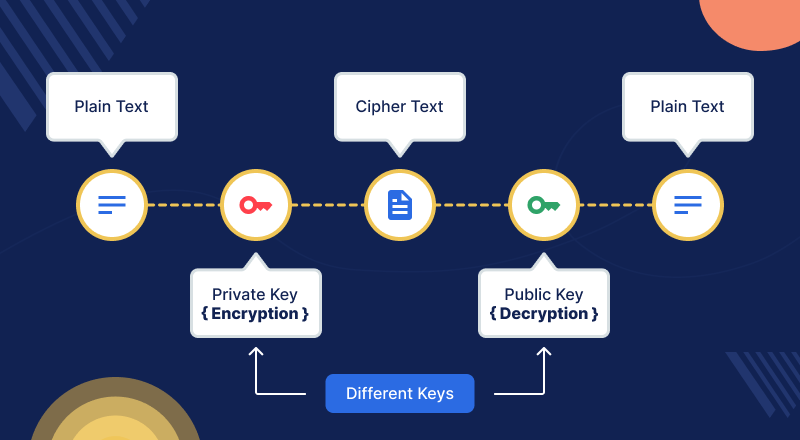
- Data Encryption: Encrypt data both in transit and at rest to protect sensitive information.
- Continuous Monitoring: Deploy security monitoring systems to detect and respond to threats in real time.
- Employee Training: Educate staff on best practices, potential risks, and the importance of securing IoT devices.
The Future of IoT Cybersecurity
As IoT adoption continues to grow, the importance of IoT cybersecurity will only increase. Emerging technologies such as AI-driven threat detection, blockchain-based security, and zero-trust architectures will play a vital role in protecting connected ecosystems.
Businesses that invest in securing their IoT devices today will be better positioned to reap the benefits of a connected world—improving efficiency, innovation, and customer trust—while minimizing the risks of cyberattacks.
Conclusion
IoT cybersecurity is both a challenge and an opportunity for businesses in the modern digital age. By understanding the threats, implementing strong security measures, and leveraging advanced tools, organizations can protect their networks, safeguard data, and take full advantage of the transformative potential of IoT technology.