The Impact of Quantum Computing on Cybersecurity: A New Era of Threats
Quantum computing in cybersecurity is poised to reshape the digital landscape. While traditional computing systems rely on bits to process information as 0s or 1s, quantum computers use qubits, which can exist in multiple states simultaneously thanks to quantum superposition. This allows quantum computers to perform certain calculations exponentially faster than classical computers.
For cybersecurity, this presents both unprecedented opportunities and serious threats. On one hand, quantum computing can enhance cryptography, encryption, and threat detection. On the other hand, it could render many of today’s encryption standards obsolete, posing risks to sensitive data, financial systems, and national security.
Potential Threats of Quantum Computing in Cybersecurity
1. Breaking Traditional Encryption
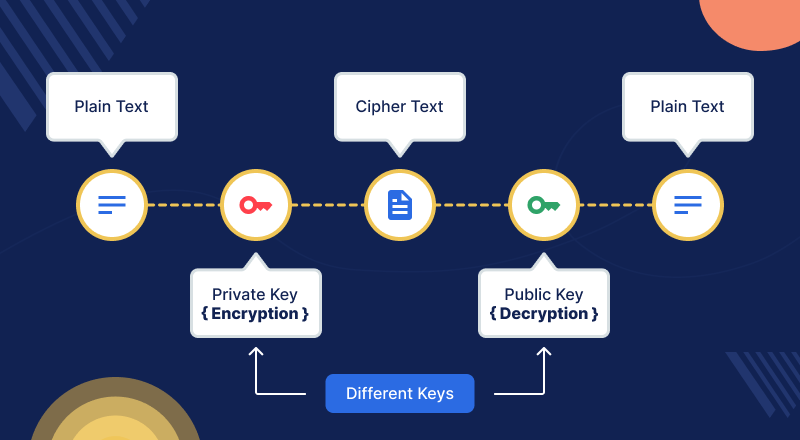
Many cybersecurity systems rely on asymmetric encryption algorithms like RSA and ECC (Elliptic Curve Cryptography). These algorithms are secure for classical computers but are vulnerable to quantum attacks. Quantum algorithms, such as Shor’s algorithm, can theoretically factor large numbers and solve discrete logarithms exponentially faster, making traditional encryption easily crackable.
2. Threats to Data Privacy
Sensitive data, including financial information, medical records, and government communications, could be at risk once powerful quantum computers are available. Organizations that rely solely on classical encryption methods may face severe breaches if they fail to adopt quantum-resistant protocols.
3. Increased Sophistication of Cyberattacks
Quantum computing could enable advanced simulation and optimization techniques, allowing cybercriminals to design more complex attacks. This might include enhanced brute-force methods, better decryption tools, and automated attack strategies that outpace classical defenses.
Quantum computing introduces a profound shift in the cybersecurity landscape by threatening the cryptographic foundations that secure today’s digital systems. Many widely used encryption algorithms, such as RSA and ECC, rely on the computational difficulty of factoring large numbers or solving discrete logarithm problems—tasks that classical computers struggle with but quantum computers could solve efficiently using algorithms like Shor’s. As quantum technology matures, sensitive data encrypted today could be decrypted in the future, creating long-term security risks for governments, financial institutions, and businesses. This emerging threat is driving the urgent development of post-quantum cryptography, pushing organizations to rethink encryption strategies and prepare for a new era where quantum-resistant security becomes essential.
Opportunities of Quantum Computing in Cybersecurity
1. Quantum-Resistant Encryption
Quantum computing is not just a threat—it also provides opportunities for enhanced security. Quantum-resistant algorithms, such as lattice-based, hash-based, or code-based cryptography, are being developed to withstand quantum attacks. By adopting these post-quantum encryption methods, organizations can future-proof their sensitive data.
2. Advanced Threat Detection
Quantum computing can enhance cybersecurity analytics by rapidly processing large datasets to detect anomalies, malware patterns, and emerging threats in real time. Quantum-enabled machine learning can help security systems respond faster and more accurately than classical counterparts.
3. Secure Communications with Quantum Key Distribution
Quantum Key Distribution (QKD) leverages principles of quantum mechanics to create virtually unhackable communication channels. Any attempt to intercept a quantum key changes its state, alerting the sender and receiver to a security breach. This represents a new era of secure communication for critical infrastructures and financial networks.
Preparing for a Quantum-Powered Cybersecurity Future
Organizations must take proactive steps to prepare for the impact of quantum computing in cybersecurity:
- Audit current encryption: Identify systems that could be vulnerable to quantum attacks.
- Adopt post-quantum cryptography: Begin integrating quantum-resistant algorithms where possible.
- Invest in quantum-aware cybersecurity tools: Leverage AI and advanced analytics to monitor threats.
- Educate teams: Train cybersecurity professionals on the implications and defense strategies for quantum technologies.
Conclusion
Quantum computing in cybersecurity represents both a revolutionary opportunity and a critical challenge. While the power of qubits could compromise current encryption standards, it also offers the potential for stronger defenses, advanced threat detection, and unbreakable communication protocols. Businesses, governments, and cybersecurity experts must act now to adapt and prepare, ensuring that the next era of technology enhances security rather than undermines it.
By understanding and implementing quantum-aware strategies today, organizations can safeguard sensitive information and stay ahead in a quantum-powered digital future.