Cloud Security: Data Protection, Access Control, and Compliance
As organizations increasingly move their data and workloads to the cloud, cloud security has become one of the most critical concerns for IT teams, executives, and compliance officers. With the flexibility, scalability, and cost benefits of cloud computing, businesses face new challenges in securing sensitive data, managing user access, and ensuring regulatory compliance.
In this blog, we’ll explore the core concepts of cloud security, strategies for protecting cloud environments, best practices for access control, compliance considerations, common challenges, and emerging trends in cloud security.
What Is Cloud Security?
Cloud security refers to the set of policies, technologies, and procedures designed to protect cloud-based systems, applications, and data from cyber threats, unauthorized access, data breaches, and other vulnerabilities. Unlike traditional on-premises security, cloud security must address challenges unique to distributed and multi-tenant environments.
Cloud security encompasses several key areas:
- Data protection: Safeguarding sensitive information stored in the cloud.
- Access control: Ensuring only authorized users and applications can access cloud resources.
- Compliance: Meeting industry and regulatory standards such as GDPR, HIPAA, and ISO 27001.
Importance of Cloud Security
Cloud security is vital for several reasons:
- Data Breach Prevention: Unauthorized access to cloud data can result in financial losses, reputational damage, and legal penalties.
- Maintaining Business Continuity: Security incidents can disrupt operations, impacting productivity and customer trust.
- Regulatory Compliance: Many industries require organizations to implement strict security controls to protect sensitive data.
- Protecting Intellectual Property: Organizations often store proprietary data in the cloud, which must be secured against theft or leakage.
- Enabling Secure Remote Work: With cloud-based collaboration, employees can work from anywhere—but only securely if cloud security practices are in place.
Key Components of Cloud Security
1. Data Protection
Data protection is the cornerstone of cloud security. Cloud environments store large volumes of sensitive data, including customer information, financial records, and intellectual property. Key measures include:
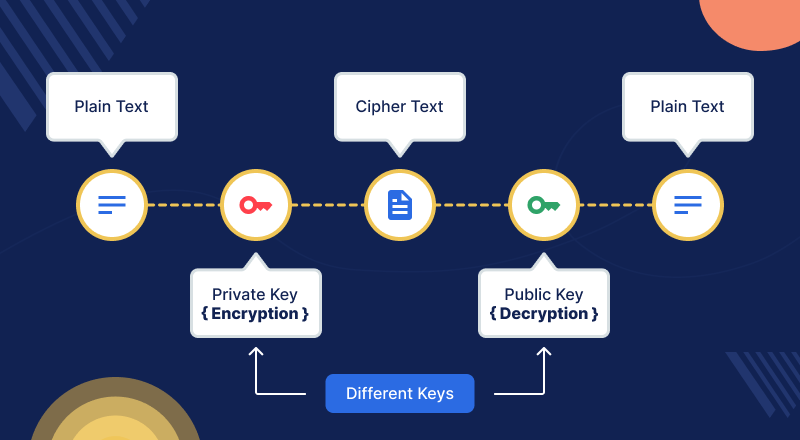
- Encryption: Encrypting data both at rest (stored) and in transit (being transferred) ensures that even if data is intercepted, it remains unreadable.
- Data Backup and Recovery: Regular backups and disaster recovery plans protect against data loss due to cyberattacks, system failures, or accidental deletion.
- Data Masking and Tokenization: Sensitive data can be masked or replaced with tokens in non-production environments to prevent unauthorized access.
- Data Loss Prevention (DLP): DLP tools monitor, detect, and block sensitive data from leaving the cloud environment.
2. Access Control
Effective access control ensures that only authorized users, devices, and applications can access cloud resources. Critical practices include:
- Identity and Access Management (IAM): Centralized IAM systems manage user authentication, authorization, and roles.
- Multi-Factor Authentication (MFA): MFA adds an extra layer of security by requiring multiple forms of verification.
- Role-Based Access Control (RBAC): Users are granted permissions based on roles, minimizing unnecessary access.
- Zero Trust Model: Assumes no user or device is inherently trustworthy, enforcing continuous verification for every access request.
3. Compliance and Governance
Organizations storing sensitive data in the cloud must comply with regulatory requirements. Cloud compliance ensures that businesses avoid legal penalties and maintain customer trust. Key steps include:
- Understanding Regulatory Requirements: Familiarity with GDPR, HIPAA, SOC 2, ISO 27001, and other relevant frameworks.
- Audit Trails and Logging: Maintaining logs of access, modifications, and system activities for compliance verification.
- Cloud Security Policies: Defining clear policies for data handling, storage, access, and incident response.
- Regular Compliance Checks: Conducting periodic audits and risk assessments to ensure adherence to regulatory standards.
Cloud Security Threats and Challenges
Despite advanced security measures, cloud environments face unique threats:
1. Data Breaches and Cyberattacks
Cybercriminals target cloud platforms to steal sensitive information. Misconfigured cloud storage, weak credentials, and unpatched vulnerabilities are common attack vectors.
2. Insider Threats
Employees or contractors with access to cloud resources may intentionally or unintentionally cause data breaches. Role-based access control and monitoring can mitigate these risks.
3. Misconfiguration
Improperly configured cloud settings, such as open storage buckets or weak firewall rules, are a leading cause of security incidents.
4. Shared Responsibility Confusion
Cloud providers and customers share security responsibilities. Organizations may assume the provider handles all security, leaving gaps that attackers can exploit.
5. Multi-Cloud Complexity
Organizations using multiple cloud providers may struggle with consistent security policies, monitoring, and compliance across platforms.
Cloud Security Best Practices
To ensure robust cloud security, organizations should implement the following best practices:
- Data Encryption: Encrypt all sensitive data in transit and at rest.
- Regular Security Audits: Conduct penetration testing and vulnerability assessments.
- Strong Identity and Access Management: Implement MFA, RBAC, and least-privilege principles.
- Secure APIs: Cloud applications rely on APIs that must be secured against unauthorized access and abuse.
- Patch Management: Regularly update cloud applications and infrastructure to fix security vulnerabilities.
- Monitoring and Threat Detection: Use cloud-native or third-party tools to detect unusual activity, threats, or anomalies.
- Incident Response Plan: Establish a clear plan for responding to security breaches or compliance violations.
- Employee Training: Train staff on cloud security policies, phishing prevention, and data handling best practices.
Real-World Examples of Cloud Security Implementation
Amazon Web Services (AWS)
AWS implements a shared responsibility model where AWS manages physical infrastructure security while customers manage data and access control. AWS provides robust encryption, IAM, logging, and compliance tools to help organizations secure cloud workloads.
Microsoft Azure
Azure offers multi-layered security solutions including Azure Security Center, Azure Active Directory, and built-in compliance management. Organizations can monitor threats, enforce access policies, and ensure regulatory compliance.
Google Cloud Platform (GCP)
GCP provides encryption by default, advanced IAM, and AI-based threat detection. Google also offers compliance certifications for HIPAA, GDPR, and SOC 2 to ensure businesses meet industry standards.
Emerging Trends in Cloud Security
- Zero Trust Architecture: Continuous verification of users, devices, and applications.
- AI and Machine Learning in Security: AI-driven threat detection and response for faster mitigation.
- Cloud Access Security Brokers (CASB): Tools that provide visibility and control over cloud applications.
- Confidential Computing: Encrypting data during processing, not just in storage or transit.
- DevSecOps: Integrating security into development and operations for continuous protection.
The Future of Cloud Security
As cloud adoption continues to grow, cloud security will remain a top priority for organizations of all sizes. Businesses are increasingly adopting hybrid and multi-cloud strategies, requiring consistent security policies across platforms.
Future cloud security will focus on:
- Automation and AI-driven threat management to reduce response times.
- Integrated compliance frameworks to simplify regulatory adherence.
- Enhanced encryption and confidential computing to protect sensitive workloads.
- Greater focus on employee awareness to prevent insider threats and phishing attacks.
Cloud security is evolving from a technical requirement to a strategic business imperative, ensuring organizations can innovate safely while protecting critical assets.
Conclusion
Cloud security is essential for safeguarding sensitive data, enforcing access control, and ensuring compliance in today’s cloud-driven business environment. Organizations must adopt a comprehensive strategy that includes data protection, strong identity management, and adherence to regulatory standards.
By implementing best practices, continuously monitoring cloud environments, and staying updated on emerging threats, businesses can leverage the cloud’s scalability, flexibility, and innovation potential without compromising security.
As cloud adoption grows, cloud security will remain a key differentiator for organizations, enabling safe digital transformation and protecting both business and customer data from ever-evolving cyber threats.