Cryptography: Developing Systems to Secure Data and Communications
In an increasingly digital world, data security and privacy have become top priorities for individuals and organizations alike. From financial transactions to personal communications, sensitive information is constantly transmitted over networks. Ensuring that this data remains confidential and tamper-proof is where cryptography comes in.
Cryptography is the science of securing data and communication using mathematical algorithms. It enables encryption, authentication, and integrity verification of information, ensuring that only authorized parties can access and understand it.
In this blog, we will explore how to develop a cryptographic system, types of encryption, common algorithms, implementation strategies, and best practices to secure data and communications effectively.
What is Cryptography?
Cryptography is the practice and study of techniques to protect information and communication from unauthorized access or modification. It transforms plaintext (readable data) into ciphertext (unreadable data) using encryption algorithms, making it unintelligible to unauthorized users.
Key goals of cryptography include:
- Confidentiality: Ensuring that data is only accessible to authorized parties.
- Integrity: Protecting data from tampering or modification.
- Authentication: Verifying the identity of users or systems.
- Non-repudiation: Ensuring that actions or messages cannot be denied after being sent.
Cryptography forms the backbone of modern cybersecurity, securing everything from emails and mobile apps to banking transactions and cloud storage.
Types of Cryptography
Cryptography can be classified into three primary types:
1. Symmetric Key Cryptography
- Uses the same key for encryption and decryption.
- Faster and efficient for large volumes of data.
- Key challenge: secure key distribution.
Popular Symmetric Algorithms:
- AES (Advanced Encryption Standard): Widely used standard for securing data.
- DES/3DES (Data Encryption Standard): Older algorithms, less secure today.
- ChaCha20: Lightweight, fast, and suitable for mobile devices.
Use Case: Encrypting files on disk or securing internal communication between systems.
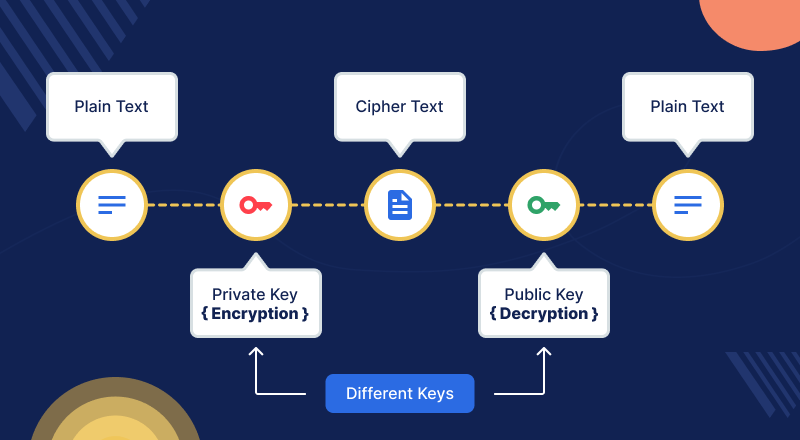
2. Asymmetric Key Cryptography (Public Key Cryptography)
- Uses two separate keys: a public key for encryption and a private key for decryption.
- Ensures secure communication without prior key exchange.
- Slower than symmetric encryption but essential for secure key exchange.
Popular Asymmetric Algorithms:
- RSA (Rivest-Shamir-Adleman): Secure and widely used for encrypting data and digital signatures.
- ECC (Elliptic Curve Cryptography): Efficient, suitable for mobile and IoT devices.
- Diffie-Hellman: Used for secure key exchange between parties.
Use Case: Securing emails, HTTPS communication, and digital signatures.
3. Hash Functions
- Converts input data into a fixed-length string, called a hash, which represents the original data.
- Hashing is one-way, meaning it cannot be reversed to retrieve the original data.
- Commonly used for data integrity verification and password storage.
Popular Hash Algorithms:
- SHA-256/ SHA-3: Secure cryptographic hashes used widely in blockchain and security systems.
- MD5 (deprecated): Older algorithm, no longer considered secure.
- BLAKE3: Fast and secure hashing algorithm for modern applications.
Use Case: Password storage, digital certificates, and blockchain transaction verification.
Developing a Cryptographic System
Building a cryptographic system requires careful planning, secure algorithm selection, and proper implementation. Here’s a step-by-step approach:
Step 1: Define Security Goals
- Determine what needs protection: data at rest, data in transit, or both.
- Identify threats: eavesdropping, tampering, insider attacks.
- Set objectives for confidentiality, integrity, authentication, and non-repudiation.
Step 2: Select Encryption Algorithms
- For symmetric encryption: AES-256 is recommended for strong security.
- For asymmetric encryption: RSA-4096 or ECC-256 provides robust protection.
- Use cryptographically secure hash functions like SHA-256 for integrity.
Step 3: Secure Key Management
- Keys must be generated securely, stored safely, and rotated regularly.
- Use key management solutions (KMS) or hardware security modules (HSM) for enterprise-grade security.
- Avoid hard-coding keys into software.
Step 4: Implement Encryption and Decryption
- Symmetric encryption for high-speed data transfer.
- Asymmetric encryption for secure key exchange and authentication.
- Combine symmetric and asymmetric encryption (hybrid encryption) for efficiency and security, as done in SSL/TLS protocols.
Step 5: Use Digital Signatures
- Digital signatures provide authentication and non-repudiation.
- Generate a hash of the message and encrypt it with the sender’s private key.
- Recipient verifies using the sender’s public key.
Step 6: Test and Audit
- Conduct thorough testing to ensure encryption works correctly and keys are handled securely.
- Audit logs and encryption processes regularly to detect vulnerabilities.
Popular Cryptographic Libraries
Developers can leverage existing cryptographic libraries instead of building algorithms from scratch:
- OpenSSL (C/C++): Widely used library for SSL/TLS and general cryptography.
- Crypto++ (C++): Provides symmetric, asymmetric, and hashing algorithms.
- PyCryptodome (Python): Easy-to-use cryptographic library for Python.
- Bouncy Castle (Java): Offers a wide range of cryptographic primitives for Java applications.
- libsodium: Modern library for secure and high-performance cryptography.
Use Cases of Cryptography
1. Secure Communication
- Encrypting emails, chat messages, and VoIP calls.
- HTTPS protocols for secure web browsing.
2. Data Protection
- Encrypting sensitive files and databases.
- Cloud storage encryption to prevent unauthorized access.
3. Digital Signatures
- Verifying document authenticity.
- Enabling blockchain transactions and smart contracts.
4. Authentication
- Secure login systems using hashed passwords.
- Multi-factor authentication with cryptographic tokens.
5. Blockchain and Cryptocurrencies
- Ensuring transaction integrity and privacy.
- Protecting digital wallets using private keys.
Best Practices in Cryptography
- Use Strong Algorithms: Avoid deprecated algorithms like MD5 or DES.
- Regular Key Rotation: Change keys periodically to minimize risk.
- Secure Key Storage: Use HSMs, secure vaults, or KMS for key management.
- Avoid Rolling Your Own Crypto: Use trusted libraries rather than custom algorithms.
- Combine Encryption and Integrity: Use authenticated encryption modes like AES-GCM.
- Stay Updated: Cryptography evolves; adopt new standards and patches promptly.
Conclusion
Cryptography is the cornerstone of modern cybersecurity, enabling secure communication, data protection, and authentication. By carefully designing and implementing a cryptographic system using encryption algorithms, hashing, and digital signatures, organizations can safeguard sensitive data against cyber threats.
Whether you’re developing a secure messaging platform, financial application, or blockchain system, leveraging robust algorithms, secure key management, and best practices ensures the confidentiality, integrity, and authenticity of your information.
Investing in cryptography today is not just a security measure—it’s a strategic necessity in a digital-first world.